If you are starting to use of virtual machine, you should familiar with some basic networking concept. In virtualization, there is four networking modes available in every hypervisor. NAT, Bridged networking, Internal networking, and Host only. These modes help you to manage your network setting in guest machine, within guest machines, between guest and host machine and between guest and public network or private network.
Wednesday, 12 April 2017
Saturday, 8 April 2017
Hypervisor , also
known as a hypervisor Virtual Machine Monitor (VMM).
A hypervisor is computer software or firmware on
which virtual Machin runs
There
is two types of Hypervisor. Type 1 and Type 2.
Type 1 hypervisor:
hypervisors run directly on the system hardware – A “bare metal” embedded
hypervisor,
means
that it has direct access to the hardware.
The hypervisor is small as its main task is sharing and managing hardware resources between different operating systems.
Type 1 hypervisors are gaining popularity because building the hypervisor into the firmware is proving to be more efficient. According to IBM, Type 1 hypervisors provide higher performance, availability, and security.
A major advantage is that any problems in one virtual machine or guest operating system do not affect the other guest operating systems running on the hypervisor.
Friday, 7 April 2017
What is Virtualization?
Virtualization
allows multiple operating system instances to run concurrently on a single
computer. it is a means of separating hardware from a single operating system.
Each “guest” OS is managed hypervisor. Because the virtualization system sits between
the guest and the hardware, it can control the guests’ use of CPU, memory, and
storage, even allowing a guest OS to migrate from one machine to another.
Benefit:
As
virtualization disentangles the operating system from the hardware, a number of
very useful new tools become available. Virtualization allows an operator to
control a guest operating system’s use of CPU, memory, storage, and other
resources, so each guest receives only the resources that it needs. This
distribution eliminates the danger of a single runaway process consuming all
available memory or CPU. It also helps IT staff to satisfy service level
requirements for specific applications.
Wednesday, 4 September 2013
Configure static IP for me
IP address: 192.168.1.50
subnet mask: 255.255.255.0
Dns: 192.168.1.50
Thursday, 4 April 2013
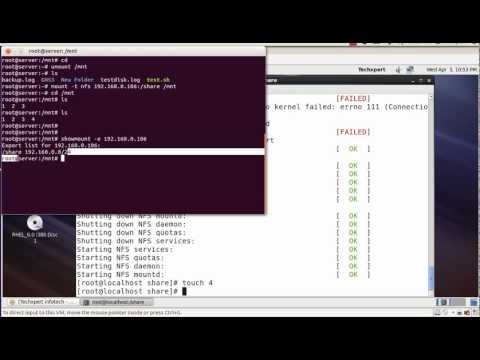
nfs server is on 192.168.0.106
[root@localhost ~] yum install nfs*
[root@localhost ~]nano /etc/exports
/share 192.168.0.0/24(rw,sync)
[root@localhost ~] mkdir /share
[root@localhost ~] chmod 777 /share/
[root@localhost ~] service rpcbind start
[root@localhost ~]service nfs restart
client side
showmount -e 192.168.0.106
mount -t 192.168.0.106:/share /mnt
Wednesday, 3 April 2013
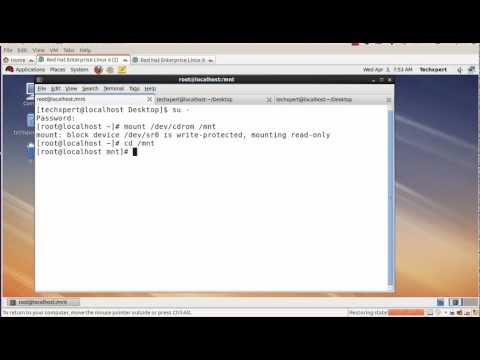
yum server and ftp server are on 192.168.0.106
Mount the rhel 6 dvd
[root@localhost ~]mount /dev/cdrom /mnt
Install ftp server
[root@localhost ~]cd /mnt/Server/Packages/
[root@localhost ~]rpm -ivh vsftpd-2.2.2-6.el6.i686.rpm
[root@localhost ~]service vsftpd start
[root@localhost ~] chkconfig vsftpd on
copy whole dvd at /var/ftp/pub
[root@localhost ~] cp -av /mnt/* /var/ftp/pub/
Create repo file for localhost (client)
[root@localhost ~]cd /etc/yum.repos.d/
[root@localhost ~]nano techxpert.repo
[techxpert]
baseurl=file:///var/ftp/pub
gpgcheck=0
enabled=1
[root@localhost ~]yum list
[root@localhost ~]yum install wireshark
ON client side:-
[root@localhost ~]nano /etc/yum.repos.d/tech.repo
[tech]
baseurl=ftp://192.168.0.106/pub
gpgcheck=0
enabled=1
#baseurl=ftp://ftpserveriporname/pub
Tuesday, 2 April 2013
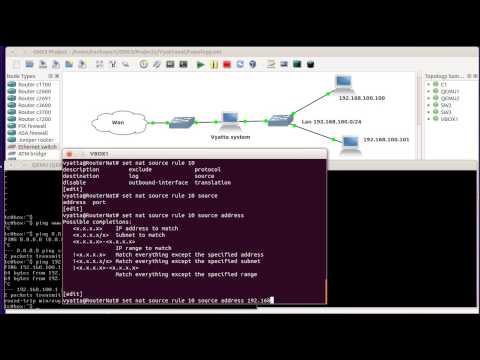
vyatta@RouterNat# set nat source rule 10 source address 192.168.1.0/24
[edit]
vyatta@RouterNat# set nat source rule 10 outbound‐interface eth0
[edit]
vyatta@RouterNat# set nat source rule 10 translation address masquerade
[edit]
vyatta@RouterNat# commit